Master Key or Breaking Smartphone Encryption
Submitted by Leonard Daly on Tue, 02/23/2016 - 07:50 Imagine the situation where every house lock is made by one of three manufactures - Ambroid, Microlock, and Orange. All of the locks take your fingerprint to open, but each analyzes your fingerprint a little differently. Now the police need to enter your home (with justification). They do not have a fingerprint match, so they require Orange to create a keyhole for every lock that when using the proper key, the door will open.
Imagine the situation where every house lock is made by one of three manufactures - Ambroid, Microlock, and Orange. All of the locks take your fingerprint to open, but each analyzes your fingerprint a little differently. Now the police need to enter your home (with justification). They do not have a fingerprint match, so they require Orange to create a keyhole for every lock that when using the proper key, the door will open.

 November's terrorism attack in Paris elicited efforts by US officials to restrict or provide alternate means for decrypting messages. People in the Congress and the Intelligence Agencies repeated older requests for backdoors that would allow them to decrypt messages and content on devices.
November's terrorism attack in Paris elicited efforts by US officials to restrict or provide alternate means for decrypting messages. People in the Congress and the Intelligence Agencies repeated older requests for backdoors that would allow them to decrypt messages and content on devices.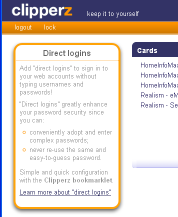 There are several services that meet these needs. Like the desktop solutions, some cost and some are free. These tools work by encrypting passwords you enter into your browser and saving those encrypted passwords on a server.
There are several services that meet these needs. Like the desktop solutions, some cost and some are free. These tools work by encrypting passwords you enter into your browser and saving those encrypted passwords on a server.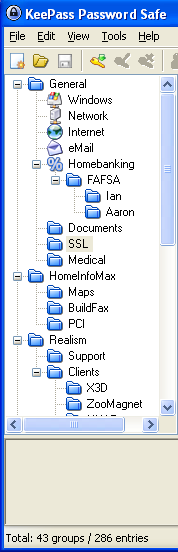 The first part of this series is
The first part of this series is  Facebook allows you to "like" a page, post, picture, or almost anything else. When you like a page, a notice gets posted to your wall. This applies to both Facebook and external pages. Facebook also gives external page authors a widget to add to their page that makes liking the page easy. When you click on that widget, Facebook records that fact, puts a notice on your wall and increments the 'like' counter for that page.
Facebook allows you to "like" a page, post, picture, or almost anything else. When you like a page, a notice gets posted to your wall. This applies to both Facebook and external pages. Facebook also gives external page authors a widget to add to their page that makes liking the page easy. When you click on that widget, Facebook records that fact, puts a notice on your wall and increments the 'like' counter for that page.